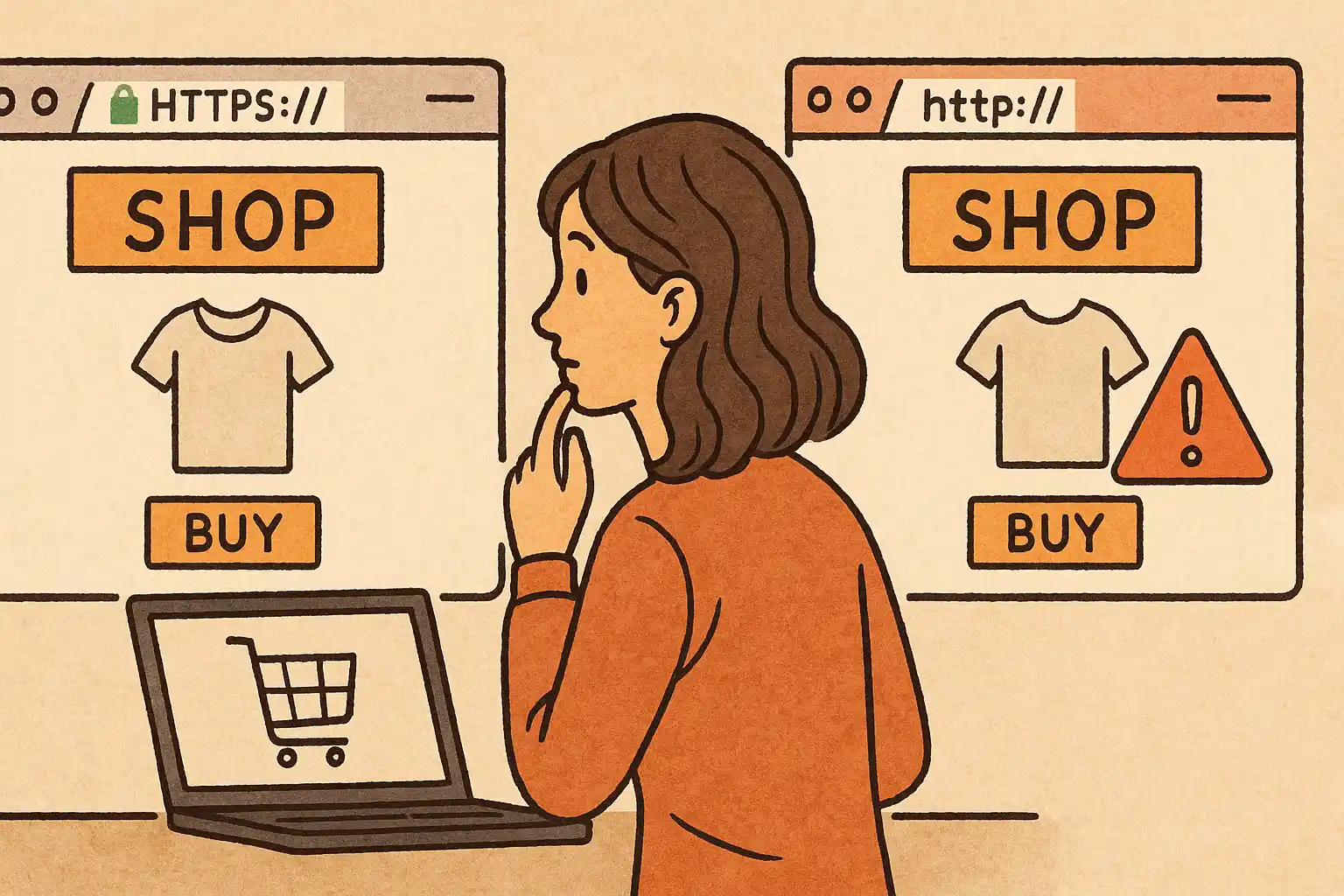
Online shopping has revolutionized how we browse, compare, and buy—from last-minute gifts to daily essentials—all from the comfort of our homes. But with that convenience comes a host of cybersecurity concerns. As e-commerce continues to thrive, so does cybercrime and various types of online fraud. How can you distinguish branded items from fake ones, or copper coins from gold ones? Understanding how to protect yourself isn’t just smart—it’s necessary.

And before we dive deeply in each of shopping practice, here is an overview of each one:
| Safe Practices | Risky Practices |
| Shop on trusted sites | Use unfamiliar or suspicious sites |
| Check for HTTPS & lock icon | Ignore security indicators |
| Use credit cards/PayPal | Pay via wire transfer or cash |
| Shop from home network | Shop on public Wi-Fi |
| Research sellers | Skip background checks |
| Save transaction records | Discard receipts and emails |
| Use Coin ID Scanner for checking quality of rare items | Buying expensive and rare items on distrusted websites |
Shop Only on Secure and Reputable Websites
Your first line of defense during online shopping is the platform you choose to trust with your money and data.
✅ Key Tips:
| Element | What to Check | Why It Matters |
| URL Security | Look for “https://” and the 🔒 padlock icon | Indicates SSL encryption; your data is protected during transfer |
| Domain Verification | Type the website URL directly | Clicking on links in emails or ads can lead to phishing traps |
| Company Info | Verify physical address and customer support availability | Scam websites often lack transparency |
| Customer Reviews | Use platforms like Google Reviews or Trustpilot | Real user feedback can help identify shady operations |
Pro Tip: Bookmark trusted online stores rather than relying on random search results or social media links. Scammers often create near-identical clones of well-known sites to trick you into entering payment info.
Use Strong, Unique Passwords and Enable Two-Factor Authentication (2FA)
Passwords are your digital keys. If you’re using the same key for every door, a breach in one system opens access to all the rest. This is a mistake most users make—and one that cybercriminals exploit daily.
🧠 Best Practices:
- Create strong passwords: At least 12 characters, a mix of upper/lowercase letters, numbers, and symbols.
- Avoid repetition: Don’t reuse passwords across sites.
- Enable 2FA: Add a second layer of verification—like a text code or authenticator app—to keep your accounts safer even if your password is exposed.
🔧 Suggested Tools:
| Tool | Function |
| LastPass / Bitwarden | Store and auto-generate secure passwords |
| Google Authenticator / Authy | Manage 2FA codes across multiple accounts |
Insight: According to a report by Verizon, over 80% of hacking-related breaches are caused by stolen or weak passwords. Don’t let your login credentials be your Achilles’ heel.
Avoid Public Wi-Fi for Transactions
That free café Wi-Fi might be great for checking memes—but it’s terrible for shopping. Public networks are unsecured by default, making it easy for bad actors to intercept any data you transmit—including login credentials and credit card numbers.
🛑 Do’s and Don’ts:
- ❌ Don’t log into shopping or banking sites on public Wi-Fi.
- ✅ Do use your mobile data or a secure home network.
- ✅ If necessary, use a trusted VPN (Virtual Private Network) to encrypt your connection.
🧰 Recommended VPNs:
| VPN Provider | Key Feature |
| NordVPN | Fast, reliable, and easy to use |
| ExpressVPN | Strong encryption, especially for mobile |
| ProtonVPN | Great free version with no data limits |
Fact Check: According to Kaspersky, one in four public Wi-Fi hotspots is not secured. That means a quarter of those coffee shop or airport connections are potential minefields for your personal data.
Use Credit Cards or Trusted Payment Services
When it comes to financial protection, not all payment methods are created equal. Using credit cards and trusted third-party services provides an extra cushion of security.
💡 Why Credit Cards Are Safer:
| Method | Protection Level | Notes |
| Credit Cards | High | Can reverse fraudulent charges; many offer built-in fraud alerts |
| Debit Cards | Moderate | Connected directly to your bank account; harder to reclaim stolen funds |
| Bank Transfers | Low | Minimal consumer protection once the money is sent |
| Virtual Cards | Very High | One-time-use numbers reduce long-term exposure |
🧾 Bonus Tips:
- Services like PayPal, Apple Pay, or Google Pay encrypt transactions and limit the data shared with the retailer.
- Consider using a dedicated card solely for online purchases—this makes it easier to monitor suspicious activity.
Watch Out for Phishing and Email Scams
Phishing attacks are among the most common—and effective—cyber threats. They often arrive disguised as promotional emails, shipping confirmations, or even refund notifications from your favorite stores. Clicking on a single link can lead you to a fake site designed to steal your login credentials or infect your device with malware.
🕵️♂️ Red Flags to Recognize:
- Unfamiliar sender addresses, especially with small misspellings (e.g., @amaz0n.com)
- Urgent language like “Account Suspended!” or “Verify Now to Avoid Closure”
- Links that don’t match the domain (hover to preview before clicking)
- Attachments with strange file formats (.exe, .scr, .zip)
📩 Email Safety Checklist:
| Action | Reason |
| Don’t click suspicious links | May redirect you to phishing websites |
| Avoid downloading attachments | Could contain ransomware or spyware |
| Mark phishing emails as spam | Helps train your email filter to block future threats |
| Use spam filters and email protection | Built-in tools from Gmail, Outlook, or ProtonMail offer excellent filtering |
Insight: According to IBM, phishing accounts for over 90% of successful cyberattacks. Spotting fake emails can be the difference between safe shopping and stolen identity.
Keep Devices and Software Updated
Neglecting software updates is like ignoring a hole in your digital roof. Cybercriminals often exploit known vulnerabilities in outdated operating systems, browsers, and apps. Staying updated keeps these vulnerabilities patched and your data protected.
🔄 What to Keep Updated:
| Item | Why It Matters |
| Operating System (Windows, macOS, Android, iOS) | Fixes known security flaws |
| Web Browsers (Chrome, Firefox, Edge) | Prevents exploits during web sessions |
| Security Software | Keeps up with the latest threats like Trojans and keyloggers |
| Shopping Apps | Updated versions fix bugs and close loopholes for hackers |
🧰 Security Software Recommendations:
- Malwarebytes – Excellent malware scanning and cleanup
- Kaspersky or Bitdefender – Strong real-time threat prevention
- Windows Defender – Solid protection for casual users (when updated)
Tip: Enable automatic updates wherever possible to reduce the risk of human error.
Save Transaction Records
You might be used to clearing your email and browser history to stay tidy—but don’t toss away your digital receipts too fast. Saving records of your purchases is a simple yet powerful way to resolve future disputes, track expenses, and spot unauthorized charges early.
📋 Best Practices:
- Save screenshots of order confirmations and shipping info
- Archive email receipts in a dedicated folder (e.g., “Online Orders 2025”)
- Use budgeting tools or apps like YNAB, Mint, or Spendee to log purchases
- Review credit card or PayPal statements weekly for irregularities
🗃️ Example: What to Keep
| Type of Record | Why It’s Useful |
| Order confirmations | Proof of purchase and delivery terms |
| Tracking numbers | Validate lost or delayed packages |
| Seller correspondence | Supports return/refund claims |
| Payment confirmations | Helps in case of duplicate charges |
Real-World Tip: Some banking apps now auto-categorize your spending. Enable alerts to track purchases in real-time and flag anything unexpected.
Use Dedicated Resources and Tools
One of the smartest strategies to reduce risk is compartmentalization—separating your online shopping from other digital activities. This limits exposure if one account or device is compromised.
🧩 Simple Separation Tactics:
- Create a dedicated shopping email: Use a secondary email account for e-commerce to reduce spam and isolate login risks.
- Use a shopping-only browser or browser profile: Disable extensions and plugins not essential for security.
- Consider a dedicated device: If you frequently shop online, using a tablet or low-cost laptop solely for purchases keeps your main devices safer.
🧰 Extra Tools:
| Tool | Use Case |
| Privacy.com | Create virtual cards for one-time use |
| Ghostery / uBlock Origin | Blocks trackers and malicious ads |
| SecureGateNet Blog | Stay informed with lifestyle-driven cybersecurity tips |
Pro Insight: Cybersecurity experts recommend keeping high-risk activities like banking and shopping isolated from general browsing. Think of it like using a separate lockbox for your valuables.
Trust Your Instincts and Be Skeptical of “Too Good to Be True” Deals
Scammers thrive on emotional triggers—scarcity, urgency, and greed. That’s why phishing emails use words like “limited offer” or “only 2 left in stock.” And it’s why fake storefronts offer designer items at 90% off. If it looks too good to be true, it usually is.
🚩 Red Flags for Suspicious Deals:
- Prices significantly lower than on established platforms
- No product reviews or vague, overly positive ones
- Poor website design, low-res images, or broken English
- No clear return policy or contact information
✅ Emotional Awareness Tips:
| Scenario | Thought Process |
| “Flash Sale Ends in 5 Minutes!” | Take a breath. Check if the deal appears on other reputable platforms. |
| “Rare Item for $10!” | Cross-check with official brand sites to verify standard pricing. |
| “Seller Only Accepts Bank Transfer” | Walk away—this is a classic scammer tactic. |
Bonus Advice: If you’re unsure about a deal, take five minutes to search “[Store Name] scam” or “Is [website] legit?” in a search engine. Fraud reports often surface quickly online.
Trusted Resources You Should Bookmark
Staying safe isn’t just about one-time actions—it’s about staying informed. The cybersecurity space evolves quickly, with new scams, malware, and tools emerging almost daily. These trusted platforms will help you stay a step ahead:
📚 Recommended Sources:
| Resource | Focus Area |
| SecureGateNet Blog | Practical, lifestyle-based security insights |
| FTC Consumer Advice | Official U.S. government guidance on scams |
| Krebs on Security | Deep analysis on fraud, breaches, and industry news |
| Have I Been Pwned | Check if your email or accounts were exposed in breaches |
| Cybersecurity & Infrastructure Security Agency (CISA) | Alerts and best practices from a national authority |
Pro Tip: Subscribe to email alerts or newsletters from at least one cybersecurity source. A monthly digest is enough to keep you updated without feeling overwhelmed.
Cybersecurity doesn’t require paranoia—just preparation. Follow these expert-backed tips, reduce your digital footprint, and build defense layers. With all of these, you can feel confident navigating the world of online shopping.